Privacy is something everyone values, so as we become more and more connected online, we become more and more concerned about volunteering our information. Tech companies like Apple, Google, Facebook, and Amazon not only get the data we willingly provide, but also get lots of data we unwittingly provide.
What does Apple know from your data?
Is your data safe from the Facebook data breach?
Things you didn’t know about virtualization
Protect your Facebook data with these 3 steps

Facebook users woke up to a nightmare when they heard that the social media giant and associated app developers were selling their sensitive data to companies, like Cambridge Analytica, without their consent. So if you're concerned about being one of the 50 million users whose data have already been sold, you should check out the following 3 tips.
Cybersecurity protocols to protect PHI

As you are well aware, healthcare companies and the vast amount of valuable patient information they hold have become a major target of cyberattacks. Hospitals must combat this with a highly-trained team of technicians equipped with premium systems and protocols, including:
Routine Access Monitoring
To control access to protected health information (PHI), your IT department must introduce guidelines and restrictions.
Gearing up for phishing scams in tax season
Why your business should get SaaS-y
3 ways 5G data will change VoIP

In this digital age, mobile connectivity is a top priority for personal and business users alike. 5G, or fifth-generation wireless systems, will change not only people’s daily routines but also the way small- and medium-sized businesses operate. Here are three main ways that 5G will change VoIP for SMBs.
Improved video conferencing
The major factor holding web and video conferencing back is how fast current networks can transmit data.
Alternatives to the Optane SSD
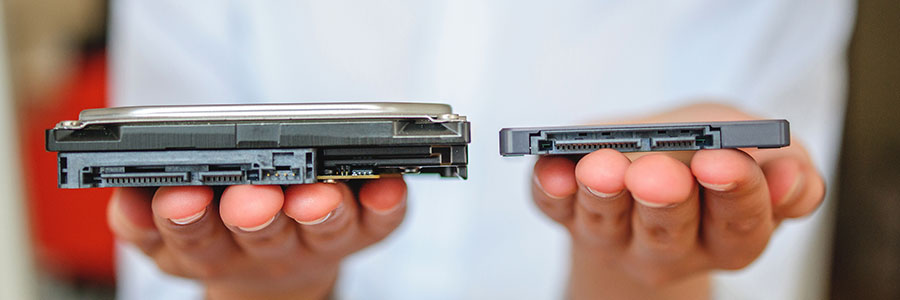
Intel has released a totally new type of hard drive designed for faster boot times and storage. People in the market for a new hard drive may consider this technology, but before making any big investments, you need to know the full capabilities of Optane SSD. Below is our review of Intel’s newest storage device.
How Fantom is haunting unsuspecting users

The heart of a lady is not easily won; a man can’t rely on his looks or wallet to make a girl fall head over heels. He must charm his way into her heart. Let’s say that a computer user is the woman, and that ransomware, the man, is the dreamboat that has worked his way through all the woman’s defenses.





