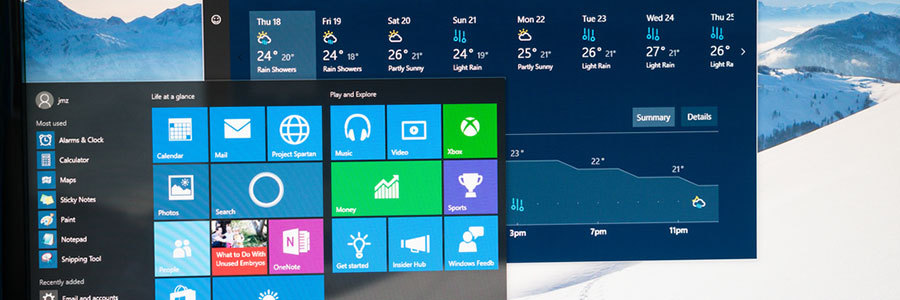
Although Google released its first high-end smartphone later than Apple and Samsung, its mobile devices have consistently been top performers. The latest version of its Pixel phones are out and there’s a lot to like for business users.
Models and pricing
The Pixel 3 comes in two models, each with two price points depending on how much storage you need.
Google Pixel: An iPhone competitor